When Mobile Apps Collude…

In the world of communication technology, we are often looking at new ways of collaborating, sharing and exchanging information with each other. Mobile Apps have now made that level of collaboration so convenient. Especially when we can do all fancy stuff with smart phones these days. People keep talking about privacy issues and that an individual must take notice of the various permissions these Mobile applications need to access from your device. But the point is even with such precautions in the “connected world”, attackers conveniently find their way to breach any possible security measure.
Organizations implement “Segregation of Duties (SoD)” as one of the important and stronger security controls to prevent frauds but that does not wipe off the possibility of frauds. At the individual level, though we are able to control frauds with SoD in place, when individuals from different departments with different duties collaborate, it results in frauds through collusion and is difficult to detect as investigators need to be able to put all the pieces of the jigsaw puzzle together.
This is very true of Mobile apps these days. The Threats Report released by McAfee Labs in June 2016 has pointed out the threat of mobile app collusion. The report defines mobile app collusion as the process in which two or more mobile apps use interapp communication in a collaborative fashion to perform any harmful activity.
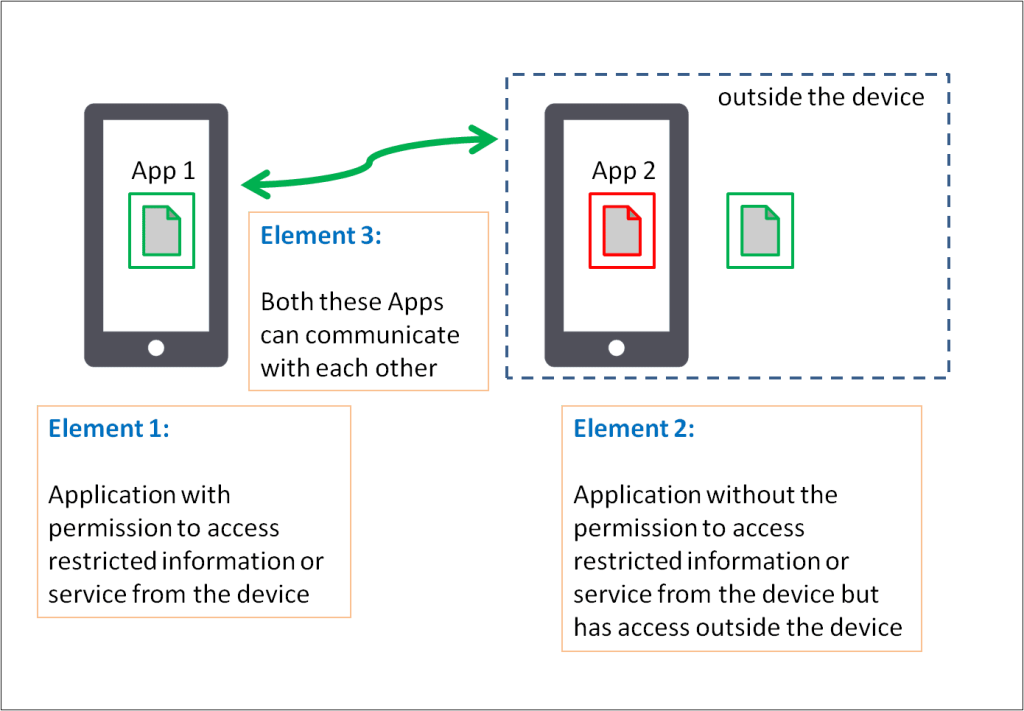
Elements of mobile app collusion:
The apps could collaborate on purpose or unintentionally due to accidental data leakage or inclusion of a malicious library. They tend to use a shared space to communicate and exchange information regarding privileges that the app has and which out of them could serve as the gateway for data exfiltration executing remote commands.
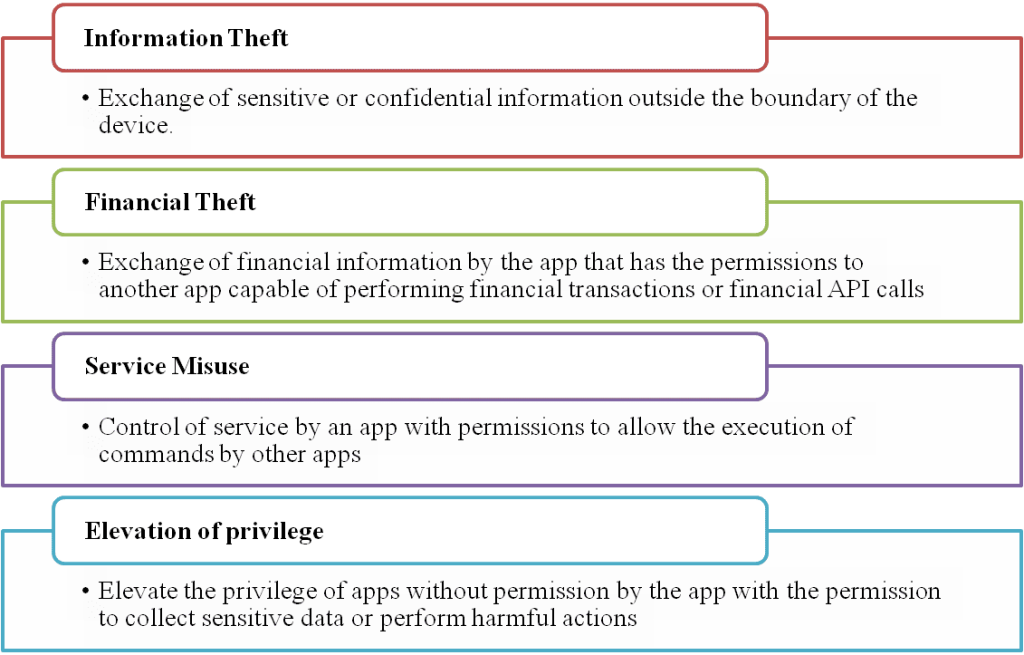
Malicious behavior exhibited by colluding mobile apps:
Safeguarding Against Colluding Mobile Apps:
As recommended by Intel® Security (briefly listed)
- Use apps from trusted app stores and publishers
- Disable the ability to install apps from “unknown sources”
- Avoid using software with embedded advertising
- Research the ratings and reviews of an app before installing
- Don’t “jailbreak” or “root” the device
- Deploy a mobile management solution
References:
[1] McAfee Labs Threats Report: June 2016 (http://www.mcafee.com/us/resources/reports/rp-quarterly-threats-may-2016.pdf) [2] Safeguarding Against Colluding Mobile Apps (http://www.mcafee.com/in/resources/solution-briefs/sb-quarterly-threats-may-2016-1.pdf)Featured image: http://newsroom.emea.intelsecurity.com/wp-content/uploads/2016/06/Capture-10.jpg