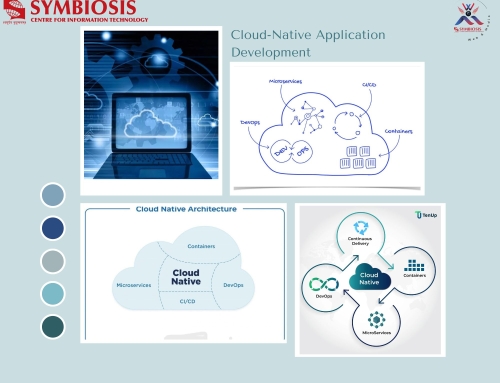
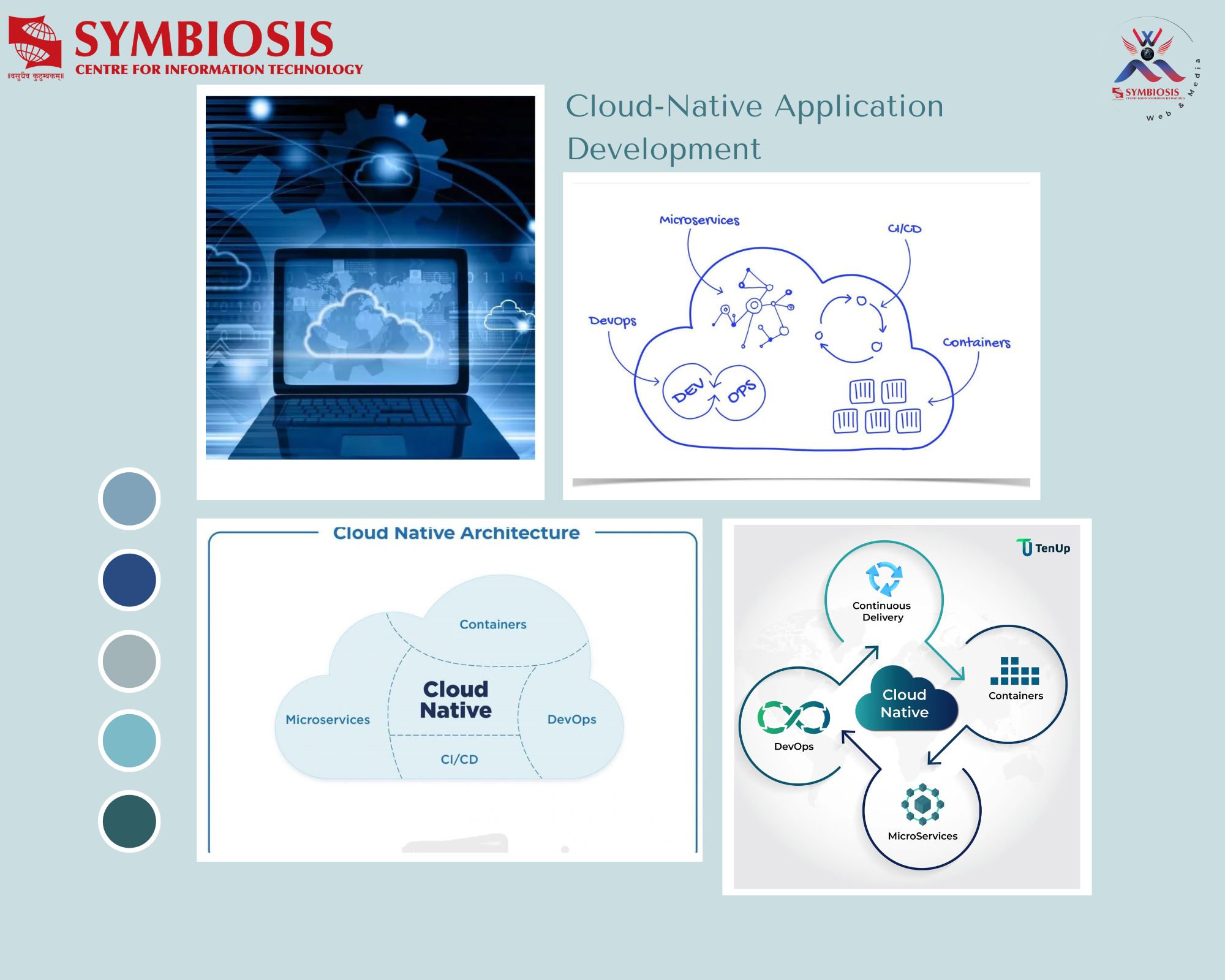
Team Matrix’s Guest Lecture on “Private Security and Privacy”

SCIT’s Team Matrix organized a Guest Lecture on “Private Security and Privacy” by Mr Aannaaand K Deshpande. The lecture also witnessed to insights on the “Significance of Certifications” in the area of IT Audit and Risk management by Mr Gaurav Thorat – SCIT Alumni and the demand for “Cyber Security” professionals by Mr. Niranjan Reddy.
The session has started with Mr. Gaurav, SCIT alumni, who briefly spoke about his career profile in the area of IT Audit where he emphasized the need for certifications in any technology or profile and showered limelight on the value that it added during a merger or slowdown when certified employees would definitely be looked upon to be retained. This is primarily because of the relevancy that a certified professional brings to the table in terms of the skills acquired.
We were also showed a video on one of the International professional associations – ISACA, and the various certifications it offers for professionals at various levels of experience. To name a few – CISA, CISM, CRISC, CGEIT and CSX were discussed briefly associated with the sectors of Governance and Risk Audit in the world of Information Security.
This was followed by a lecture from Mr. Niranjan Reddy on the career prospects as a Cyber Security Professional. For the first few minutes, we were presented with a lot of statistics revolving around Cyber Security as a career and the significance it has in the modern day world. With numerous established organizations vulnerable to data breaches all around the world, the need for the cyber security professionals has been exponentially increasing.
This was further explained when it was told that by 2020, the supply of Cyber Security professionals would still be behind the surplus demand. In this evolving arena, the speaker also emphasized the edge that a candidate possess when with a certification, hence we were also introduced to the certification on Ethical Hacking, CEH.
With that followed the session for the day on “Private Security and Privacy” by the Guest speaker Mr. Aannaaand K Deshpande, wherein we were introduced to a lot of terms in Information Security – Privacy, Confidentiality and Consent to name a few, with most of us having understood the subtle differences that each of them meant in the contexts presented. The various privacy principles with regards to Storage and Security were discussed with repeated importance given to the limits one has to possess in the disclosure of personal information. Having discussed the Information Lifecycle in detail, we then stepped into the policies associated with Privacy. This was followed by various case laws and the regulations that the judiciary possesses over fraudulent cases involving Information security breach.
An informative session where the audience were kept engaged where queries were taken and resolved by providing various incidents on data breaches as examples. Most of us got the necessary inputs required on the scope within Information Security on niche areas like Cyber Security and Forensics.