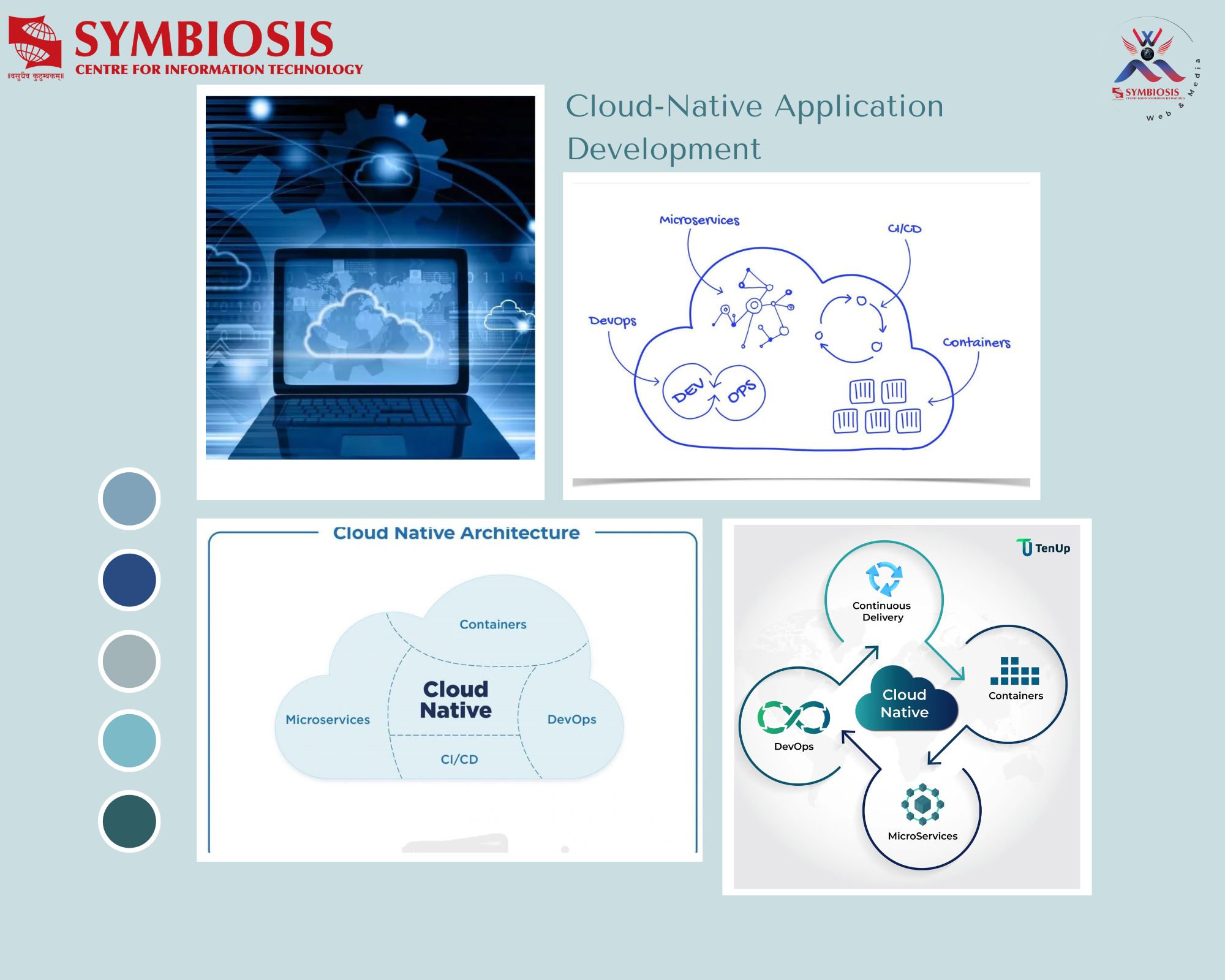
Security Audits

1. With increasing insecurity in the Cyber Domain, Cyber Security has become an essential part of our life. Digital gadgets cannot be done away with in the present scenario. At home or at office you are living in a virtual world and the dangers of this imaginary world have intruded in our day to day lives. Now we speak of Cyber Crime, Cyber Espionage and Cyber War which are the fall out of technological enhancements happening every second and at every domain. Dangers of cyber world can be mitigated but cannot be eliminated and to mitigate we have to think and implement Cyber Security at homes and at work places. To find out the vulnerabilities security audits have to be carried out.
2. Firstly you need some framework and policies in place to carried out audits. The policy of your organisation should flow from the ‘National Cyber Security Policy’ and you should have an expert team to carry out security audits. The policy should lay down the Do’s and Don’ts required for cyber hygiene.
3. Security Audits can be of three types, Internal, External and Special. Internal audit to be carried out by the organisation itself on a quarterly basis, External audit to be carried out by someone from outside on annual basis and a Special audit can be carried out if there is a serious breach of Cyber Security irrespective of when it has occurred.
4. The objectives of the Internal Security Audit should be:-
a) To identify security weaknesses.
b) To provide an opportunity to improve the ISMS. (Info Security Management System).
c) To provide management with info about the status of security.
d) To review compliance of security systems with Cyber Security of the organization.
e) To find and resolve non compliance.
5. The objectives of the External Security Audit should be:-
a) Assess process of internal audit.
b) Determine the commonality and frequency of recurrence of various types of security violation.
c) Identify the common causes.
d) Advisory and training inputs to tackle the neglect of procedures.
e) Review and update the policy.
6. Typical audit activities to include:-
a) Audit Planning.
b) Conducting Audit.
i. Document Review.
ii. Preparation of onsite audit.
iii. Onsite Audit.
c) Audit Reporting.
d) Follow up.
7. Security Audit should be carried out for all digital infrastructure be in PCs , switches, routers, networks, etc. To put it in a different way Cyber Security Umbrella consists of Info security, Database security. Application security, Desktop security (Operating System hardening), Network security, Personal security and Physical security, hence all these aspects should be included in Security Audits of an organisation.
Name: Santosh Khadsare
About the author: CEH (Certified Ethical Hacker), RHCSA (Red Hat Certified System Administrator), Life Member (Computer Society of India)