On either side of the wall
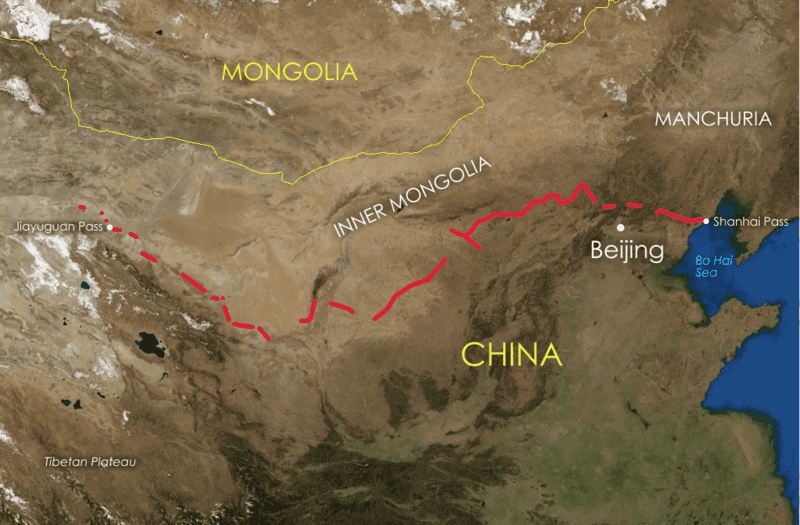
Icon picture – Geographic location of the great wall. Courtesy: wikipedia (This blog was co-created by Prof. Saravan and Dr. Dhanya Pramod. Many thanks to Prof. Vishal who sparked the idea for this blog).
The Great Wall of China is the largest man-made structure, visible from space. Many generations of labourers, peasants and prisoners had worked on it for centuries. The earliest known construction was in 3000 BCE. First there were primitive walls made of desert mud, plants and wood all packed up in layers – it didn’t last long. As each generation made the wall taller and wider, it also grew stronger and more sophisticated. Today, the modern structure, still standing, is more than 8000 kms long and built over a period of 1000 years! The walls were built layer by layer, and became stronger from one generation to the next.

Earliest known remains of the great wall dated 3000 BC (picture courtesy picture courtesy webzeest.com),
Depiction of Construction (picture courtesy national geographic ).
Why did they build the wall? Huns, plunderers from the north of China (modern name of this region is Mongolia), started raiding Chinese villages. Strong forms of protection against the fierce warriors were needed. When they raided, no army could stand against them and they left nothing but ruins in their wake. So how does the emperor protect his people? By building up a very tall, very very long wall atop the bordering mountains.
All of this history reminds us of modern IT security companies. IT security is a strategic approach to protect information stored in digital media or that which is in transit. It deals with the implementation of processes and systems that can safeguard information. While dealing with information, confidentiality, integrity and availability of information should be ensured. What do these terms mean? Can you come up with examples to understand better?
Internet and specifically “www” has paved the way for information explosion, and data communication has become a need with the emergence of globalization. Like ancient raiders, hackers lurk in all corners of the digital world. Protection of information is of the utmost importance as violation to security may lead to loss of goodwill, financial implications, legal consequences which can end up in closure of business. Like the ancient protective wall, the potential of IT security companies specialising in sophisticated storage and communication technologies bring key value to each business and government. What are the essentials to be protected in modern society and business?
Watch towers along the great wall (picture courtesy china-mike.com)
Flashback to ancient China: The wall is dotted with beacon watch towers. At night, when tower guards glimpse raiders from the other side of the wall, they would light up a bonfire on the beacon tower. Thus, the remaining watch towers are alerted and they may light up their bonfires to signal confirmation. If it was daytime, smoke signals were created. Such warning systems visible from miles away, showed clear signals of the location of the invaders and even encoded the size of the armies with smoke or lantern signals. Entire villages prepared for battle and helped their women and children flee in well planned routes. Timely information is power!
The scene is much different today, where our loved ones may not know enough to protect themselves. Small amounts of data of a citizen can be stolen to seize their digital identity, and ultimately ransack their comfortable modern life. In India, compromised personal security due to careless use of data has been observed. Have you come across such instances? Why and where did consumers go wrong with their personal security?
Today’s parents lament that children and youth are always ‘plugged in’ with technology and gadgets. Addiction to technology is a common phenomenon. It is high time to educate kids of the dangers in cyberspace. Tech-smart parents take the help of technology. Open source tools for Child monitoring and parental controls such as AVG family safety, Norton online family and Microsoft windows live family safety are very useful. What do you feel? Should parents monitor what their child is doing?
Another parent says “a major share of internet activity goes to social networks, not learning. All the while this new generation may not be realising they are becoming ‘anti’ social”. How would youth respond to this concern? Do you believe you are really connecting with the world when you are plugged in to social networks? What would you say to younger children?
(picture courtesy cyclechina.com)
In the business world, the scene is vastly different. Banking transactions use multiple authentication techniques to identify authorised users and for those who follow strong passwords and security tips will not fall prey to hackers. Some companies understand the high importance of security and have IT security strategy programs in place which are aligned with both IT strategy and Business strategy. However security does not come cheaply. Companies decide on the amount of investments in IT security, based on risk and criticality of information, and depend on encryption protocols. However, attacks may continue to happen as hackers find newer ways. What would happen if new companies did not invest well in IT security strategy?
Occasionally children end up playing havoc with IT security. In year 2000, a Swedish teenager noticed his account number is visible in the address bar of browser. He playfully changed the account number and found that he could access the other account. He managed to transfer funds too! Do you know of other interesting examples of hacking? There must be interesting incidents you may have heard or read.
According to a news article by Ravi Venkatesan, the IT party will be over in India in a decade. With constructive destruction, new technologies will replace obsolete ones. He predicts that security professionals will flourish along with entrepreneurs and others who continue evolving with the times. Economics times reported that Infosec professionals are in demand and that attractive salary packages await them.
To conclude, as long as Information and communication exists, security will be a concern. Technologies may change, but hackers will get brighter with every raid. This will justify the need for security professionals. Automation cannot completely substitute the brains of humans, whether they are hackers or infosec professionals. So there is a lot of action going on either side of the wall. Let’s chat about IT security. Looking forward to your discussion threads. Happy learning!
References: Wikipedia, national geographic, http://www.china-mike.com/china-tourist-attractions/great-wall-china/construction-history/,