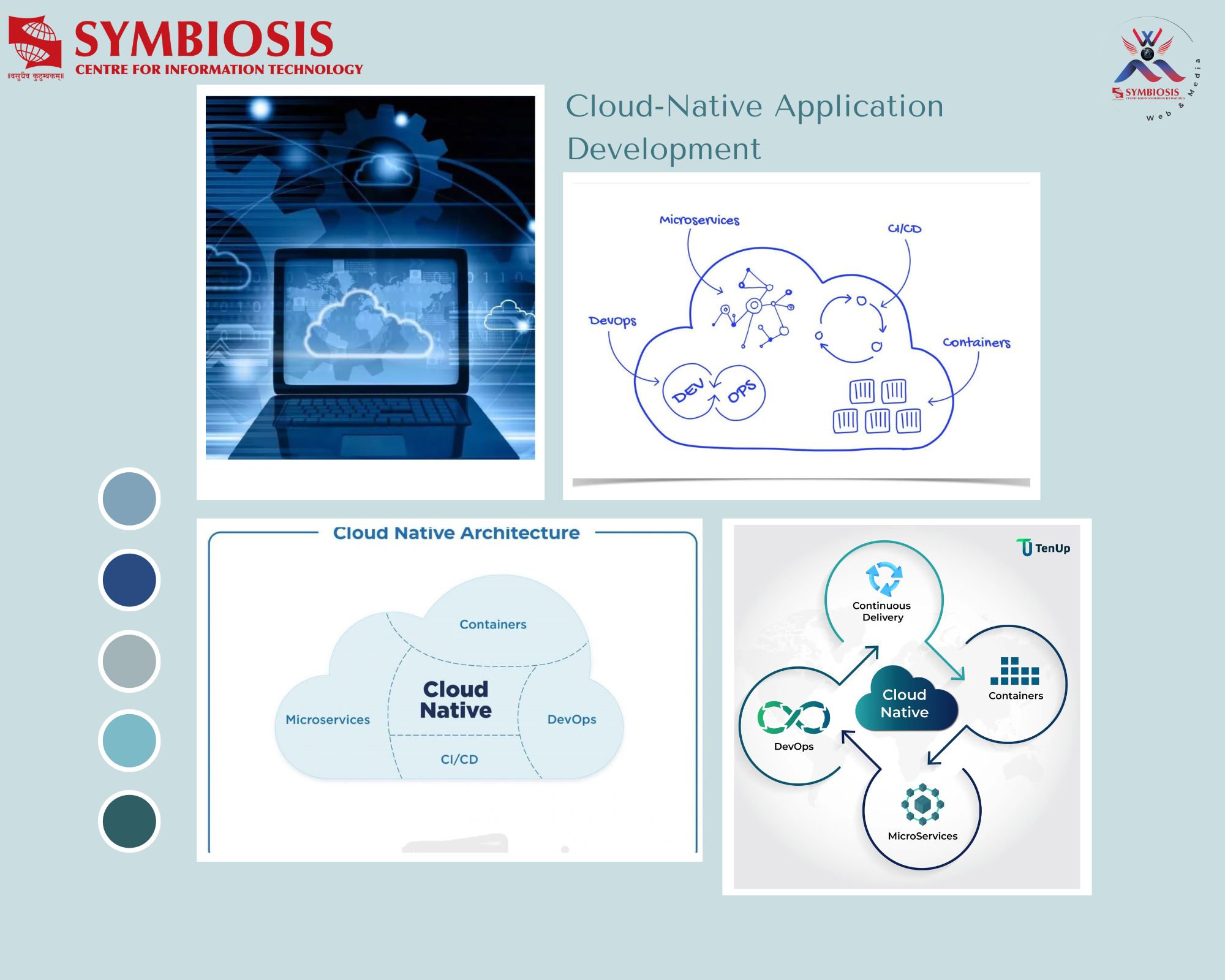
Why Hire, Just Pay Bounty

“Security is always going to be a cat and mouse game because there’ll be people out there that are hunting for the zero day award, you have people that don’t have configuration management, don’t have vulnerability management, don’t have patch management.”
-Kevin Mitnick.
We all know who Kevin Mitnick is, and the statement given above is just as true as his conquests with this Game of Security.
Security is a field where there’s a Samsung S4 after a few months of Samsung Galaxy S3, ever changing. One needs to always be in touch with the best knowledge about specific attacks and their countermeasures. Sometimes this can be a difficult task for a middle-aged or even young person working for a multi-national company and coping up with the daily working of ensuring the security of the company can be a difficult task as well.
In the word of Information Security there’s a very famous quote-
“Anything that cannot be measured is not deemed secure.”
Hence, a Person working for a firm gets busy in looking after the various details of the organization along with maintaining each part of the security along with the correct metrics and measures is always hard!
Whereas, Security Researchers know their work well and they are focused on exploiting the particular vulnerability which may be very new and known to them, and hence offering a more better secured experience through their work.
People like Jerremiah Grossman and Saumil Shah have brought some new vulnerabilities to light, attacks such as BEAST, CRIME & CLICK-JACKING later came into picture, with the growing impact of security and security researchers, new forms of exploitation were known to the world.
This is where Security Researchers and Bug Bounty comes into picture, It’s like the story of the famous movie of Avengers, you may have the best of armies of the world, but it’s the super-hero’s that come to rescue.
Bug bounty helps various sites into improving the user experience, making their customers feel safe and providing a much more secure environment for a user. It’s through the Bug bounty that a website or product gets through the testing of various penetration testers around the globe, which gives such sites to get an exposure to unknown security threats which make tester’s realize that XSS, CSRF and SQL injections are not the only vulnerability found in the web applications or products.
Sites as big as Google and Facebook offer bug bounty not because these are big firms and have enough money to spend on such schemes, but because they know no matter how old they get there always will remain a vulnerability of some or the other kind and they greatly support bugs being found and pay to them generously. Web Application Sites who are not as rich as these multimillion companies just give acknowledgement as “”HALL OF FAME” which is enough to get noticed and improve the site in the various ways possible.
Bug bounties are just a way to increase the security of your site, just like the customer support department which is kept just in case a person needs some help or has to complain regarding some issue. Bug bounties are just people around the world trying to complain to you about some security issue that they found out.
Yet, I would say is that you need not hire people and just go for bug bounty, for one may keep a panel for expert advice but they never become the CEO, it’s in the same way the Bug bounty may help the websites path security vulnerabilities but they’ll be only might be experts in their field whereas, the person who manages the various tasks after being hired for the company is responsible for his job and he will see to it that the security issues of the firm he’s hired for are looked after to the best of his capabilities.
Bio- NITESH SHILPKAR, I’m a security researcher been acknowledged by various sites like Google, Etsy, Zendesk, Freelancer etc ! and Yes, I’ve received some bug bounties also.
Name: Nitish Shilpkar
About the author: Student at IIIT-Allahabad, pursuing MS in Information Security and Cyber Law.