SOCIAL ENGINEERING

- Cognitive biases are the methodologies or rather we can say certain tendencies to think in certain manner, one of the core concepts of human psychology.
- It is the basis of social engineering a term that has become quite popular in the security world as it is often used to hamper the sanctity of sensitive information through an individual.
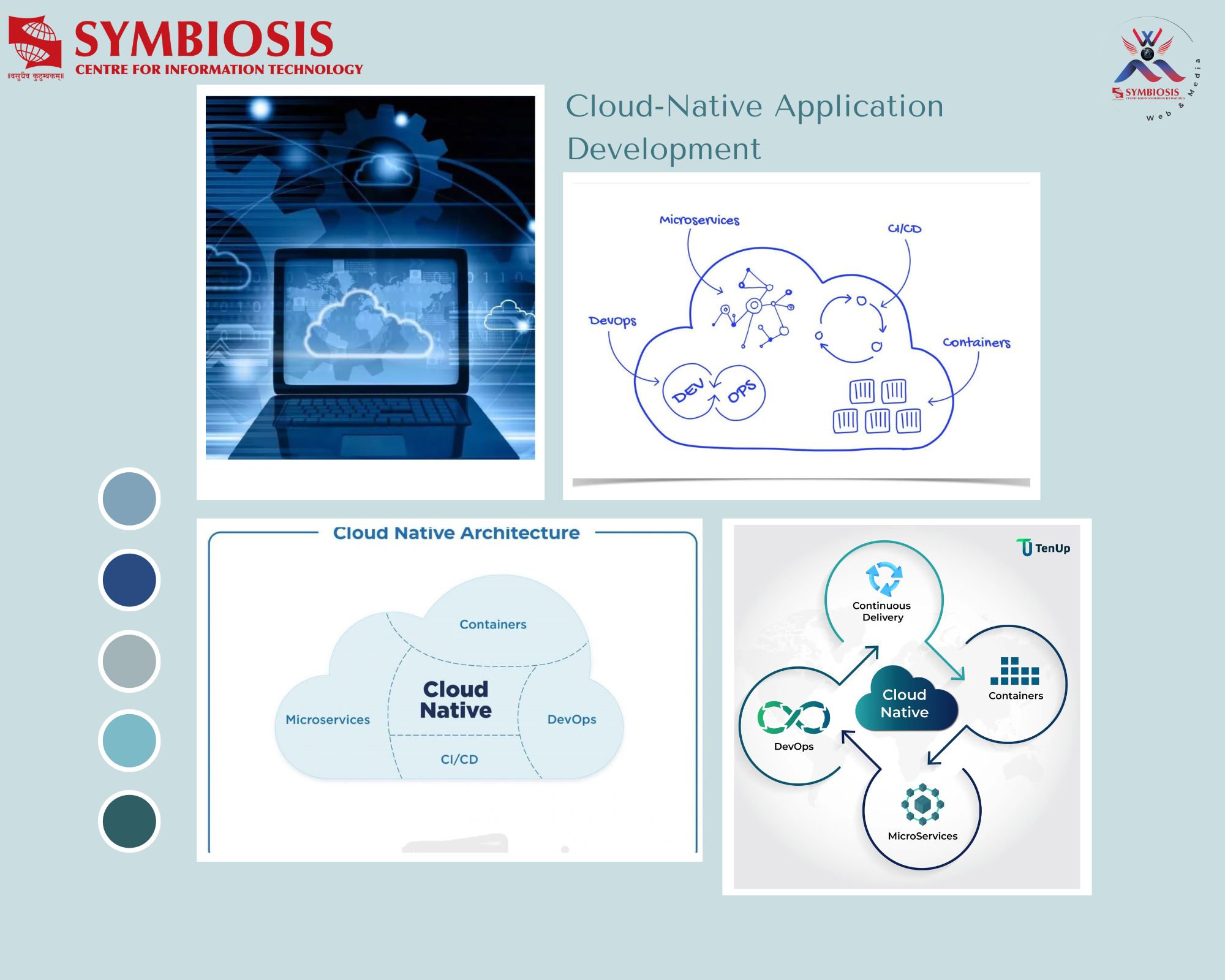
So what social engineering is :-
- “It is an act which is used to obtain sensitive information from the individuals by influencing them”.
- It has been found out that people are often doesn’t aware about the amount of information they possess and careless about protecting it.
- Most of the time what happens is that people knowingly or unknowingly reveal the secure information to their peers or outsiders which is one of the important sources for security threats.
- Though the security industry has evolved a lot in the computer world, but it has not been able to safeguard data against this social engineering aspect.
- A significance pattern that has been identified in getting sensitive information from the people either through “Shoulder Surfing” a method of looking into the codes through someone’s shoulders and through memorizing someone’s passwords which are most of the time people personal data.
- It has also been found out that in most of the attacks, the victim’s personal information is clubbed with some other information and used for penetrating a network.
Some of the common techniques that are often used for social engineering:-
a) Familiarity with the victim: It has often been found out that most of the time the attacker make familiar himself in a particular location and then winning the confidence of the people try to gain the access of the important information from the people. Victim also unknowingly shares the valuable information and ultimately bears the result.
b) Phishing: It is one of the most common ways of getting confidential information from the users by sending the fraudulent emails. People unknowingly share their information by replying to those mails which helps in giving access to the attacker. Also sometimes it happens that the attacker creates a fake page of a website and sends it to a user and when the user clicks and fills it cards details, the details go to the attacker.
c) Pretexting: –It is also a popular method of getting personal details of the victim by getting his confidence and getting personal data like date of birth, cards data, bank details etc.
d) Tailgating: One of the most common security issues in an enterprise. In this an attacker, gets inside a restricted area by following an authorized person of that area.
e) Baiting:-In this the attacker sends a malicious code like virus or malware etc through a hardware device like CD, Floppy, Hard disk etc. When the user inserts the hardware device, the malware or virus gets installed into the user system, thus giving access to the attacker to the victim’s system.
Security Controls:–
Following security measures can be taken in order to protect the sensitive information from the social engineers:-
a) Proper training of the employees in an organization.
b) Latest deployment of controls for safeguarding people personal information.
c) Performing periodic tests or dry runs from time to time to check the controls in an organization.
d) Better governance through better policies, best practices etc.
e) Creating awareness among people by the organizations and government or private agencies.
f) Strict penalties or sentence to the people found guilty.
g) Understanding of responsibilities by the larger organizations.
Conclusion:-
So it is clear, that as the world of information will increase, the social engineers will become more aggressive. Hence it is required that people become more aware and cautious in handling their personal information.
Name: Nitin Saxena
About the author: Nitin is currently pursuing his MBA in IT Business Management at SCIT, Pune