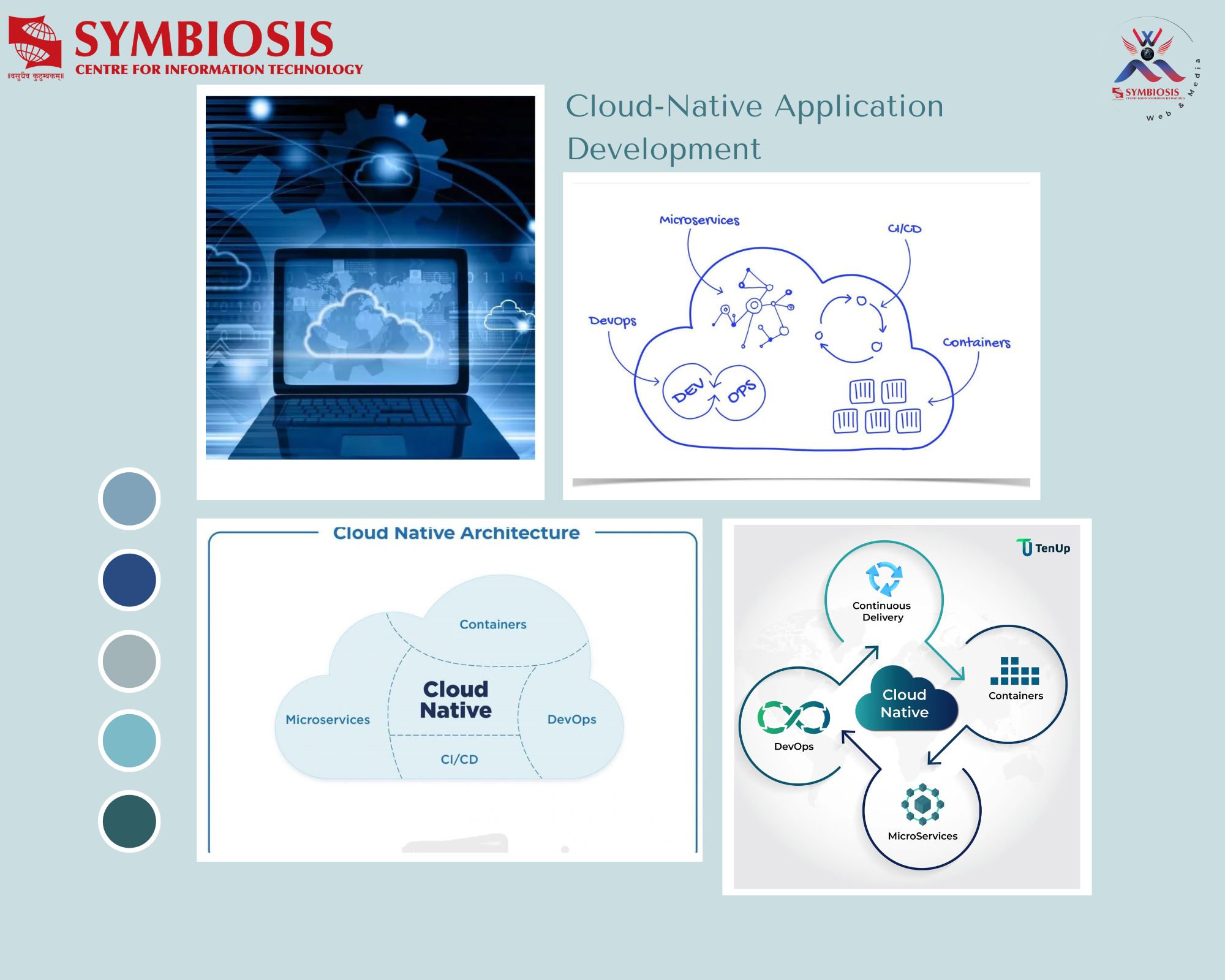
BYOD- a new issue in IT

What is BYOD ?
Decades back on the shop floor a cryptic jargon BYOD was in vogue, it said “bring your own dinner” .This was meant to tease the employee , particularly in the night shifts, who had nothing to supplement their hunger. Amazingly this cliché BYOD has come back in the IT sector with a new flavor, Bring Your Own Device . As the workspace crunch and flexi-timings are becoming more and more prevalent, providing a permanent workstation for all employee is becoming problem for the facility managers. Employees with laptops, tablets and various other mobile devices are joining the team of the regulars and connecting these devices to the enterprise network, all for the project work. This no doubt relaxes the adherence for continuous procurement of standardized equipment and at the same time opens the information risks. Thus, at once this becomes an issue of promises vs. pitfalls .Employees and sometimes even the senior executives express their preferences of using the devices of their own choice, whereas the ISS is challenged with the consequences of widespread uses of such personal devices. Hence evolving a BYOD strategy is today a topic of discussion in the IT sector. A BYOD strategy need to be accommodating the new trends in the lifestyle and working habits at the same time not compromising the enterprise information security risks. All concerned are trying chart out best practices to adopt which will satisfy the internal users with simple easy to manage and adopting a secured mobile solution.
“Consumerization” of IT
The consumerization of IT is coming to your business.
This is new coinage of term in IT, quoting from an article in the Computerworld of October 2011,which surveys the unprecedented clamour for the mobile devices such as ipad, smartphone, and various types of tablets in the market. The survey concludes that almost 50% of the respondent to the survey show that their employers allow them to work on their own devices either in the company premises or away from the office.
This is done on the realization that employee productivity and job satisfaction increases with this latitude. At the same time, the organizations by this approach reduce the cost of development and a virtual team from different geographical location can be leveraged for development following agile methodology. Business is benefited by the flexible working hours and allowing the employee to use the device of their own- anytime ,anywhere.
Challenges :
Even though this trend has not caught up in India to an extent that the CIO s and the users take steps to address the issue and work out the solution to the challenges it might pose. As the employee would choose to bring their own devices to work the primary concern would be the security challenges. Since these devices would be connected to the enterprise network, it would be difficult to enforce the uniform level of security measures on these devices as installed on the company devices. When there are many devices , these are likely to have different OS on them. Thus, the network administrator won’t have any control to ensure the same level of security features on them. There could be different software loaded on the personal devices which would be able to penetrate the security ring around corporate database, applications, etc. Such personal devices could be able to by pass the privileged accesses .Virus carried on the consumer devices could spread over the network causing enterprise-wise threat. Thus, allowing BYOD as company policy the premier challenge is more of technical in nature , which can briefly be reckoned as:
i) Support of a wide range of devices having different OS, viz, Windows, Mac, iOS, Android ,etc,
ii) The Network Manager has to ensure the authenticity of the endpoint devices seeking access. Such integrity checks have to be carried out based on well documented BYOD policy
iii) The traffic scan to and fro from the commercial devices through the enterprise network- calls for deep packet inspection.
iv) Robust monitoring system to filter out rogue application, virus detection
v) Managing the bandwidth allocation to application- not to be slowed down or choked if a commercial device run video.
vi) Control on Web browsing.
vii) E-mail and intranet access from employee owned devices
Other Imperatives :
While there will be considerable cost saving by the company allowing BYOD in terms of working space and equipment cost , the employee consequently can demand “reimbursement” and support for their own devices. The “reimbursement” may be an HR and financial matter the support of the devices can be problematic. Some typical question relating to the support problem can arise as shown below:
ü What levels of support should be promised – total, partial on usage basis or a running scale ?
ü Should all the employees be eligible for their own devices and have access to company data and applications? Or should this be restricted based on the role, title, managers’ approval, geographic, or other organizational considerations?
ü Desirable to restrict access selectively to particular applications or data- If so, problem of selecting employee and in case working on more than one project/apps. ?
ü Infrastructure and competence to support all individual employee owned devices ? Headache of support and maintenance outsourcing
ü Tuning and support of Interface programs for the multiple employee owned devices- handling problem when third party is involved.
Risk in Introducing BYOD:
Since the introduction of the practice of BYOD is fraught with various challenges and risks , it worthwhile to address the damage and impact associated with the risks. , Any IT department must necessarily have in place a policy and practice that ensure organizations vital data back-up and information security. This is done without affecting the employee productivity. This practice involves the participation and cooperation of other departments, including human resources, purchasing, legal, financial, and the business units. To address the damage associated with the BYOD Risks, the following points come up:
a) There should be some idea and estimate for the risks for loss of corporate data or intellectual property?
b) How would the content on employee devices be managed without interfering with personal use?
c) Must users of the own devices sign an undertaking for avoiding the risks associated with BYOD
- before connecting personal devices to the corporate network?
d) How much personal data, such as his location through GPS data, should be collected by the company about the users?
e) The risk of losing personal devices -how the lost or devices stolen owned by the employee be compensated /replaced ?
f) The risk of employee carrying non-disclosure information provided by the customer on their own devices.
g) The risks of using the devices by users other than the corporate end user ?
h) What should happen if a user violates policy? The risk of user violating BYOD Policy and practice – leading to data loss, IPR compromise, etc.
Policy on BYOD
A BYOD policy primarily should have enough provision to effect curtailing any violation or breach of information security .Companies are prone to lose valuable data, documents, designs, codes, corporate client list due to lack of policies, strategies and procedures to enforce secure use of user owned mobile devices. The BYOD policies should be documented and read by those employees desirous of using their own devices. The policy must clearly state note only the procedures but also the consequences of misuse or violation there of. Also the organization should be vigilant and act quickly to take remedial measures in case of violation to prevent further loss of information assets of the company..
Summarizing: BYOD and the Educational institutes
Although in Indian IT companies the BYOD is yet to pick-up in a big way. But this is like a wave is bound to come our shores. Today ,the students community in most of the institutes are allowed to use their own laptops and very soon we shall see the proliferation of smartphones and iPads. The network administrator today is managing the access to the institute network through MAC Id and password. In the next couple of years the challenge of the administrator will be different- handling a plethora of unfamiliar devices with variety of OS, which has to be controlled and monitored preferably at the intelligent network interfaces. The wireless security has to be augmented. This will call for a BYOD Strategy. While in the corporate world the security aspect on BYOD is varied and vast ,many of which are addressed in the advanced countries. In India the IT companies will be able to restrict the BYOD trend for some time more (since the space crunch and ownership of devices have not come in a big way) ,however, the premier educational institutes will have to evolve sooner a BYOD policy and a strategy to overcome various issues
Question: Are we prepared ?
Contributed by : Prasenjit Sen
Reference: 1.Voice and Data,March, 2012 2) www.aberdeen.com